Cybersecurity Reports Compilation
Date: October 31, 2024
1. Executive Summary
SmartMeter Co. suffered a cybersecurity breach that compromised customer billing information and sensitive company data, exposing the organization to potential regulatory scrutiny and financial risk. The attack was executed through a sophisticated phishing campaign that exploited weaknesses in user access controls and an outdated email server. This report provides a structured analysis of the breach, identifies failed security controls, and outlines a strategic remediation plan to mitigate future incidents.
Failure to address these risks immediately could result in increased regulatory pressure, financial loss, and long-term operational instability. Key findings indicate critical gaps in boundary protection:
- Weak boundary protection controls
- Lack of Mobile Device Management (MDM) policies
- Insufficient security awareness training
All these factors contributed to the data breach.
2. Site Survey & Network Topology
The following diagram provides an overview of the network infrastructure relevant to the incident:
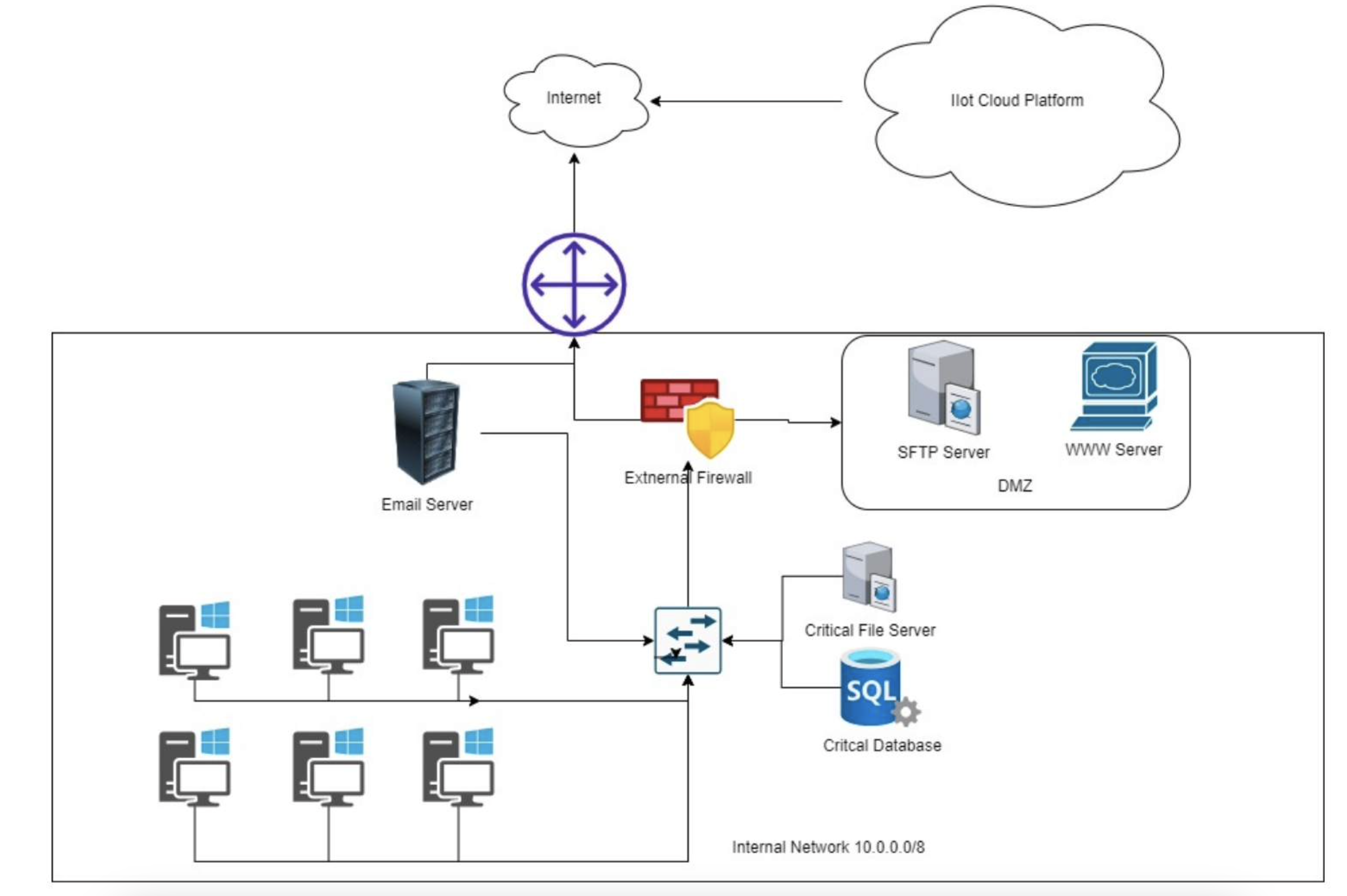
3. Incident Details
SmartMeter Co. experienced a spear phishing attack targeting specific employees through the company’s legacy email server, resulting in compromised user credentials. This breach allowed unauthorized access to critical servers, exposing the company’s intellectual property as well as customer credit and billing information.
- Date of Attack: December 14, 2023
- Severity: High
4. Root Cause Analysis
1. High-Level Observations from Logs
-
Observation 1 –
- Email server logs show an incoming email from IP: 18.8.1010 targeting specific employees.
- The email impersonated Office 365 in an attempt to deceive recipients.
- Timestamp: Dec 14, 08:00:15.
-
Observation 2 –
- The phishing emails originated from:
micr0soft@microsft.support.accounts.mercifulredeemerchurch.com
- Email subject line indicated {EXTERNAL} Office 365.
- These emails bypassed filtering and reached targeted users.
2. High-Level Interview Insights
-
Insight 1 : Lack of Phishing Attack Awareness & Incident Response Procedure -
- Executive-level staff were unaware of phishing indicators.
- Both entered credentials without hesitation due to the emails’ urgency and familiarity.
- They did not report suspicious activity even after noticing:
- Unusual emails being sent from their accounts.
- Unexpected changes in production code.
-
Insight 2 : Weak Password Practices & Lack of Accountability -
- Certain employees admitted to using the same password across multiple accounts**.
- Executive-level staff allowed others to use their mobile devices, which were also used for:
- Business activities.
- Gaming and personal use.
- Risks Identified:
- Password reuse increases exposure to credential-stuffing attacks.
- Shared device usage** raises the risk of unauthorized access to sensitive business data.
3. a) Five Whys Analysis
 Note: The “Five Whys” technique typically takes about five iterations to uncover the root cause, but it may require fewer or more iterations. It’s important to keep asking “why” until the actual root cause is clearly identified.
Note: The “Five Whys” technique typically takes about five iterations to uncover the root cause, but it may require fewer or more iterations. It’s important to keep asking “why” until the actual root cause is clearly identified.
3. b) Fishbone Analysis
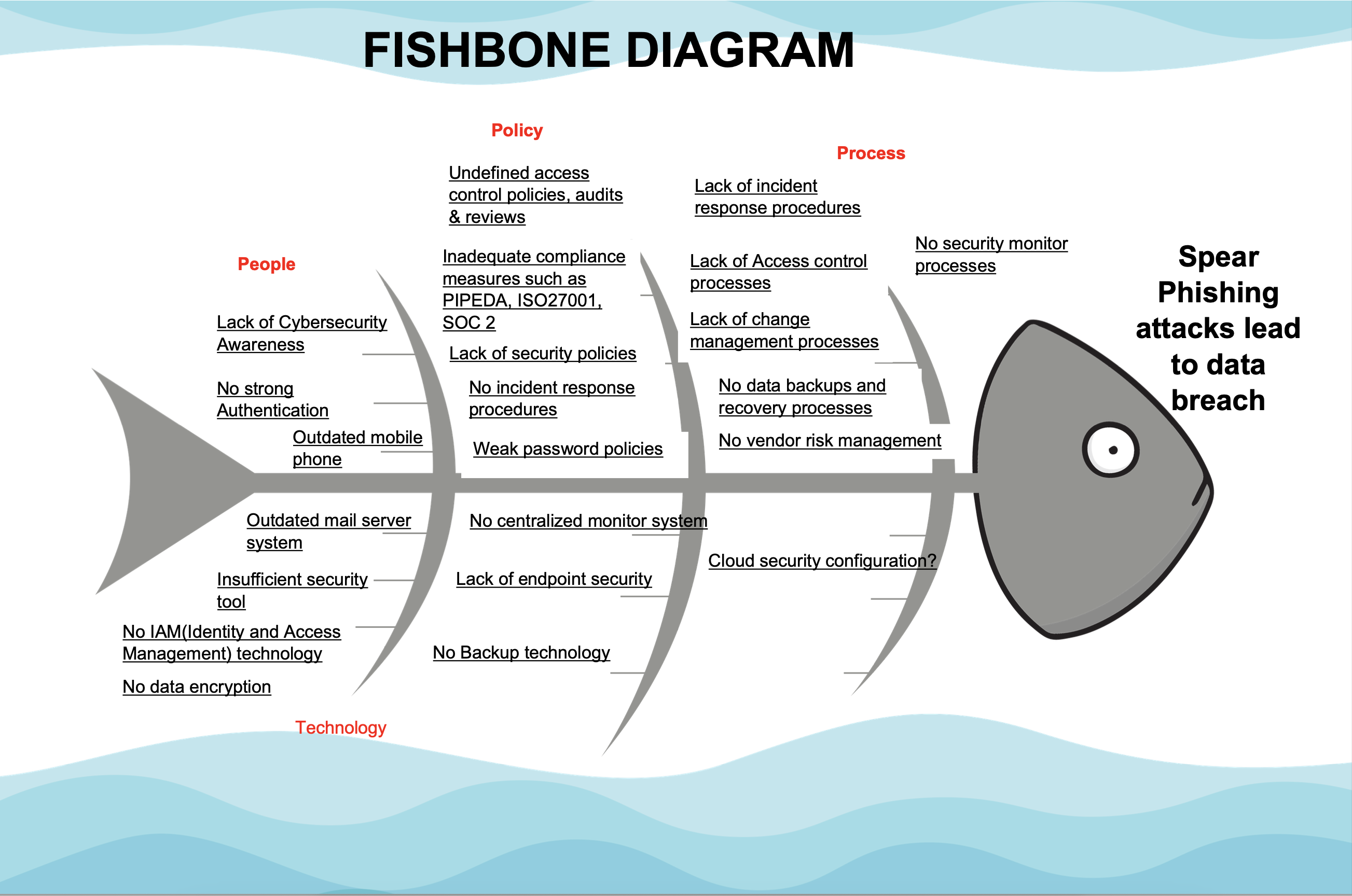 Key Insights from Fishbone Analysis:
Key Insights from Fishbone Analysis:
- Weak security policies and poor password hygiene directly contributed to unauthorized access.
- Lack of structured incident response and inadequate security monitoring caused delays in detecting and containing the breach.
5. Failed Security Controls:
Failed control 1 – AC-2 Account Management
Certain employees reused the same password across multiple accounts, and there was no enforced password policy or Single Sign-on (SSO) solution to prevent this practice. The absence of Mobile Device Management (MDM) allowed for shared access to critical servers via personal devices. It increased the risk of unauthorized access to critical systems.
Failed control 2 – AT-2 Security Awareness Training
Employees were not trained to recognize phishing emails and the potential risks. Furthermore, employees did not act promptly to report or mitigate issues when suspicious activities occurred. It resulted in delayed incident response.
Failed Control 3 – SC-7 Boundary Protection
The outdated email server lacked robust boundary protection capabilities, such as modern anti-phishing filters, email security protocols, and integration with an Intrusion Detection System (IDS) or Security Information and Event Management (SIEM) solution. This inadequacy allowed malicious phishing emails to evade security defenses and reach employee inboxes without being blocked, exposing the organization to phishing attacks. The lack of effective boundary protection, combined with limited security resources typical of a startup, increased the organization’s vulnerability to external threats, leading to unauthorized access to critical systems and sensitive data.
6. Prioritized Recommendations Based on Overall Risk
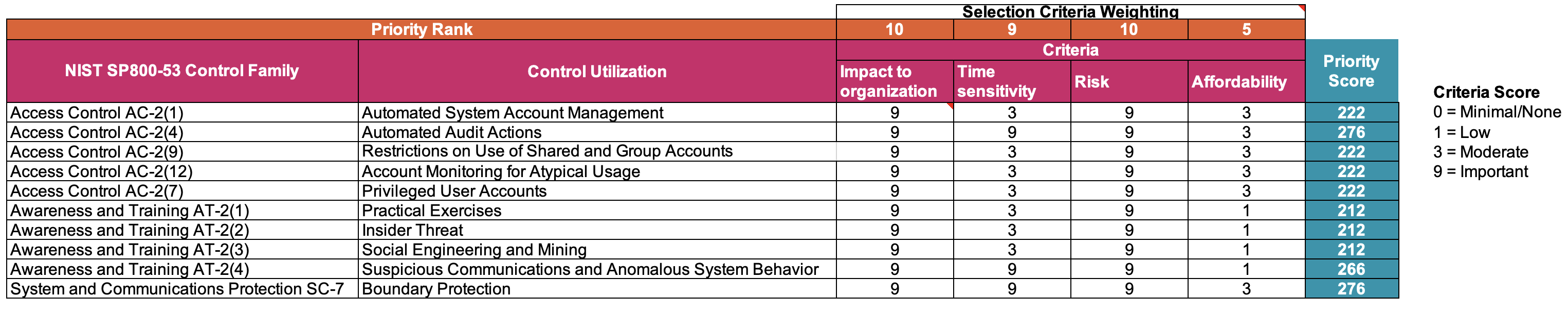
| Control | Priority Score | Brief Justification |
|---|---|---|
| Automated Audit Actions (AC-2(4)) | 276 | Real-time monitoring essential for rapid detection and response |
| Boundary Protection with Enhanced MDM, SSO, IDS (SC-7) | 276 | Crucial protection for external threat mitigation |
| Suspicious Communications and Anomalous Behavior Training (AT-2(4)) | 266 | Improves employee resistance to phishing and social engineering |
Detailed Recommendation Actions
To address the identified risks and enhance organizational security, the following actions are recommended in detail:
1. Implement Automated Audit Actions (AC-2(4)) - Priority Score: 276
Recommendation: Deploy a Security Information and Event Management (SIEM) system with centralized log aggregation to monitor and audit user accounts across the organization. This facilitates real-time alerts for unusual behaviors. Centralized log aggregation will allow analyzing logs efficiently from various sources, making incident response faster and more effective.
2. Boundary Protection with Enhanced MDM, SSO and IDS Controls (SC-7) - Priority Score: 276
Recommendation: Strengthen boundary protection by deploying a comprehensive Mobile Device Management (MDM) solution with Single Sign-On (SSO) integration and an Intrusion Detection System (IDS). The MDM will secure employee devices accessing the company’s network by enforcing policies such as strong passwords, app restrictions, and device encryption, while SSO provides streamlined, secure access across applications. Additionally, MDM includes remote wiping capabilities for lost or compromised devices. The IDS will monitor network traffic for suspicious activities, adding an extra layer of real-time detection against potential threats.
3. Suspicious Communications and Anomalous System Behavior Training (AT-2(4)) - Priority Score: 266
Recommendation: Establish security awareness training focused on recognizing suspicious communications and identifying anomalous system behaviors. Training will equip employees with skills to identify phishing attempts and respond appropriately, reducing the likelihood of successful attacks.
7. Conclusion
Implementing Automated Audit Actions (AC-2(4)), Boundary Protection with Enhanced MDM SSO and IDS Controls (SC-7), and Suspicious Communications and Anomalous System Behavior Training (AT-2(4)) is essential to quickly detect and respond to unauthorized access, secure network entry points against external threats, and equip employees with the knowledge to recognize phishing attempts.
Together, these measures will create a robust defense against data breaches, ensuring immediate action can be taken to protect sensitive organizational assets.
Delaying implementation of these measures may expose SmartMeter Co. to severe cyber risks, including further breaches, operational disruption, financial loss, and damage to corporate reputation.
 CyberSentryFox
CyberSentryFox